Cyber-Physical Systems
Data-Driven Analysis of Cascading Failures
Cyber-Physical Systems (CPSs), like smart grids, are now essential parts of modern society. The integration of computational and physical processes has great economical and societal potential. However, being open to the cyberspace made CPSs more vulnerable to attacks and failures. In smart grids, a wide range of cyber attacks and cyber intrusion may take place. In a key sub-system of many CPSs, wireless sensor networks (WSNs), various attacks may happen at different layers of the network. The variety and severity of attacks in CPSs made vulnerability analysis of great importance. What aggravates the vulnerability of CPS is cascading failure: the failure of a part of the system can cause failure in the rest of the system, by triggering successive failures of components and therefore leading to much more severe damages.
Objectives
- Design a framework to generate simpler models that can still accurately describe cascades.
- Develop methods to obtain insights from the simplified cascade models.
Dynamic Resource Allocation in Highly Mobile Environment
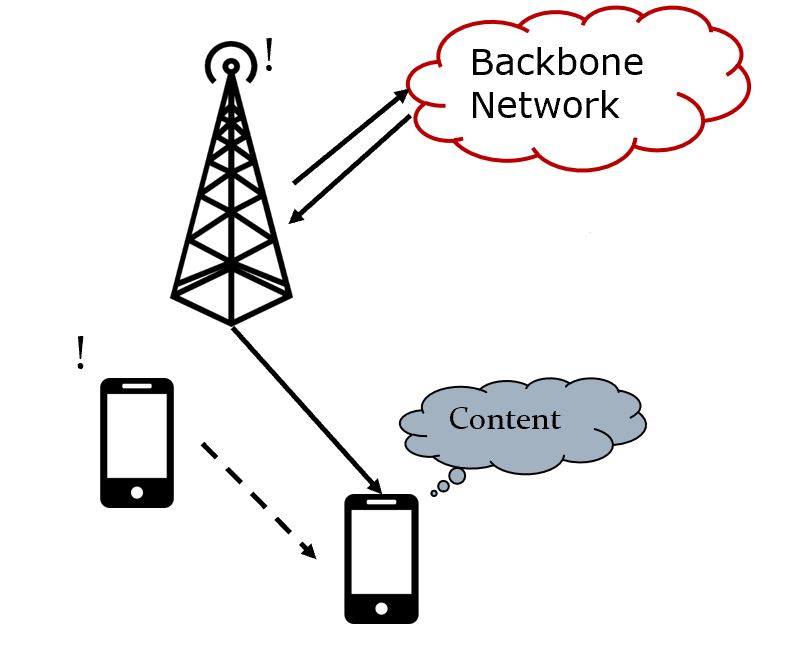
Device-to-device (D2D) communication has recently gained much attention for its potential to boost the capacity of cellular systems. D2D enables direct communication between devices while bypassing a base station (BS), hence decreasing the load of BSs and increasing the network throughput via spatial reuse of radio resources. However, the cellular system is highly dynamic, an optimal allocation plan of a radio resource to D2D links at a one-time point can easily become suboptimal when devices move. Thus, to maximize spatial reuse in cellular systems, it is crucial to update the resource allocation adaptively to reflect the current system status.
Objectives
- Design adaptive algorithms for the resource allocation problem.
- Experimentally verify the performance of spatially reuse radio resources with real and simulated mobility traces.
Online Social Networks and Cybersecurity
Privacy Vulnerability to Socialbot Attacks
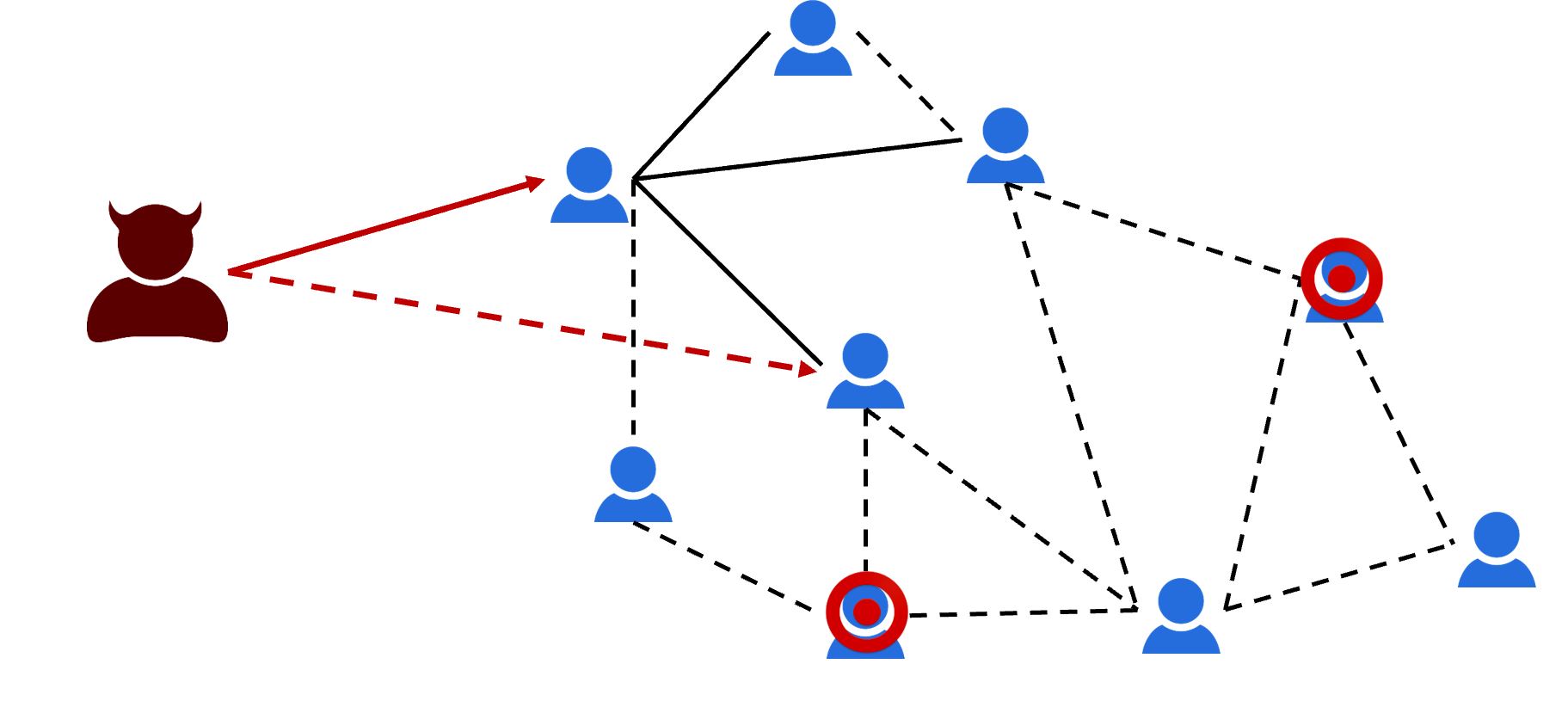
Privacy breaches are one of the biggest concerns on Online Social Networks (OSNs), especially with the introduction of automated attacks by socialbots, which can automatically extract victims' private content by exploiting social behavior to befriend them. The key insight of this attack is that by intelligently sending friend requests to a small subset of users, called the Critical Friending Set (CFS), such a bot can evade current defense mechanisms. To study the vulnerability of OSNs to socialbot attacks, a new optimization problem, Min-Friending, is introduced. The problem identifies a minimum CFS to a friend in order to obtain at least a certain amount of benefit, which quantifies the amount of private information the bot obtains. The two main challenges of this problem are: 1) how to cope with incomplete knowledge of network topology and 2) how to model users' responses to friend requests.
Objectives
- Find nodes that are the most vulnerable to social bot attacks.
- Understand attackers’ behavior and devise protection strategies.
Adaptive Crawling in Large Networks
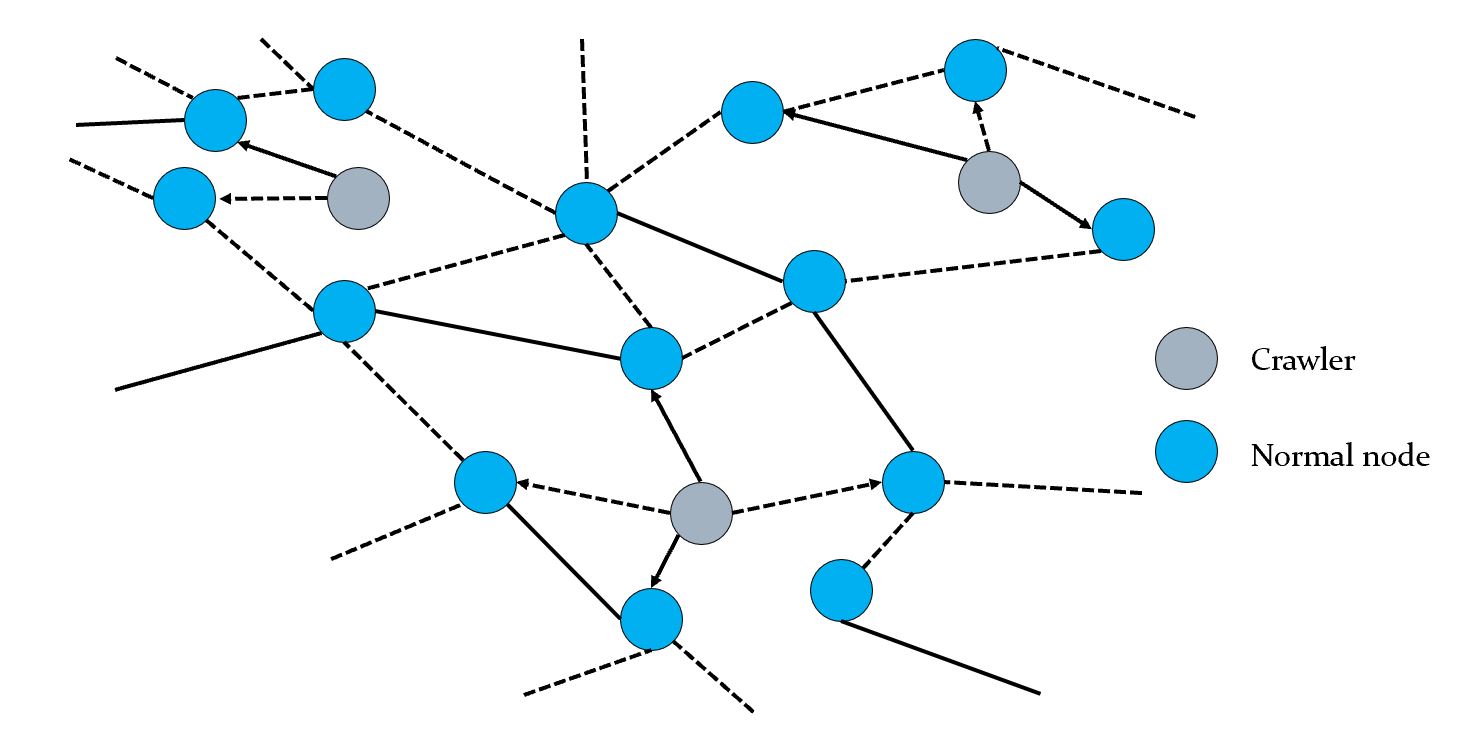
In-network probing, given an incomplete network dataset, the question is to select nodes to explore further to best enhance the incomplete network within budget constraints. This is a very crucial problem as most of the obtained datasets are often poor representations of the fully observed graph. Having access to more complete data would lead to more accurate analyses. However, the probing decisions are partly based on knowledge of the network and the probing actions may or may not be successful. Hence, it is necessary to have an adaptive strategy, in which future probing decisions are made based on outcomes of existing actions. Also, the strategy must be able to cope with giant networks such as online social networks and the Internet of Things, which are both rich repository of data.
Objectives
- Design adaptive probing strategies with theoretical performance bound.
- Ensure the efficiency of the strategies in billion-scale networks.