How to Identify an SMS Phish
How to Identify an SMS Phish
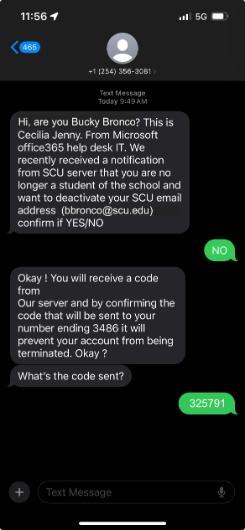
Phishing attacks aren’t limited to emails; they also target people through SMS. The example below shows a classic attempt to trick a user into sharing a Duo multi-factor authentication (MFA) code using a “man-in-the-middle” (MITM) approach. Let’s explore the red flags in this message and how to protect yourself.
Key Identifiers of This Phishing Attempt:
 |
|
|---|
What’s Happening Here?
This is a Man-in-the-Middle (MITM) attack aimed at bypassing Duo MFA. Here’s how it works:
- Attacker Has Your Password: By the time you receive this SMS, the attacker has likely obtained your password from a previous phishing attack.
- Triggering a Duo passcode: When the attacker attempts to log in using your credentials, they will need to get past Duo. So they trick you. The attacker sends you an SMS posing as IT support or some other pretend authority. When you reply, they tell you they will send a code for you to reply with to “verify” you. Then they immediately log into an SCU application using your password. When they get the Duo prompt, they tell Duo to send an SMS code, which the attacker knows will go to you.
- Tricking You into Sharing the Code: The attacker then asks you to share the code Duo has sent to you, claiming it’s needed to prevent account deactivation. Once you share it, the attacker has everything they need to access your account without your knowledge.
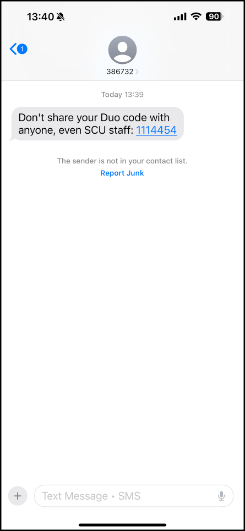
- Attack Variations: This attack scenario could work with a Push as well. If you get a text message telling you to approve a Duo Push, it’s a scam. Information Services does not contact end users via SMS. Attackers might claim to be from an SCU office or service. Always verify the legitimacy of the SCU office or service by checking contact information on the official SCU website. Do not rely solely on the message itself.
Protect Yourself
 |
|
|---|
By recognizing these red flags and understanding how Duo MFA works, you can protect your account from unauthorized access and stay one step ahead of attackers.
Nov 12, 2024